How we earn your Trust?
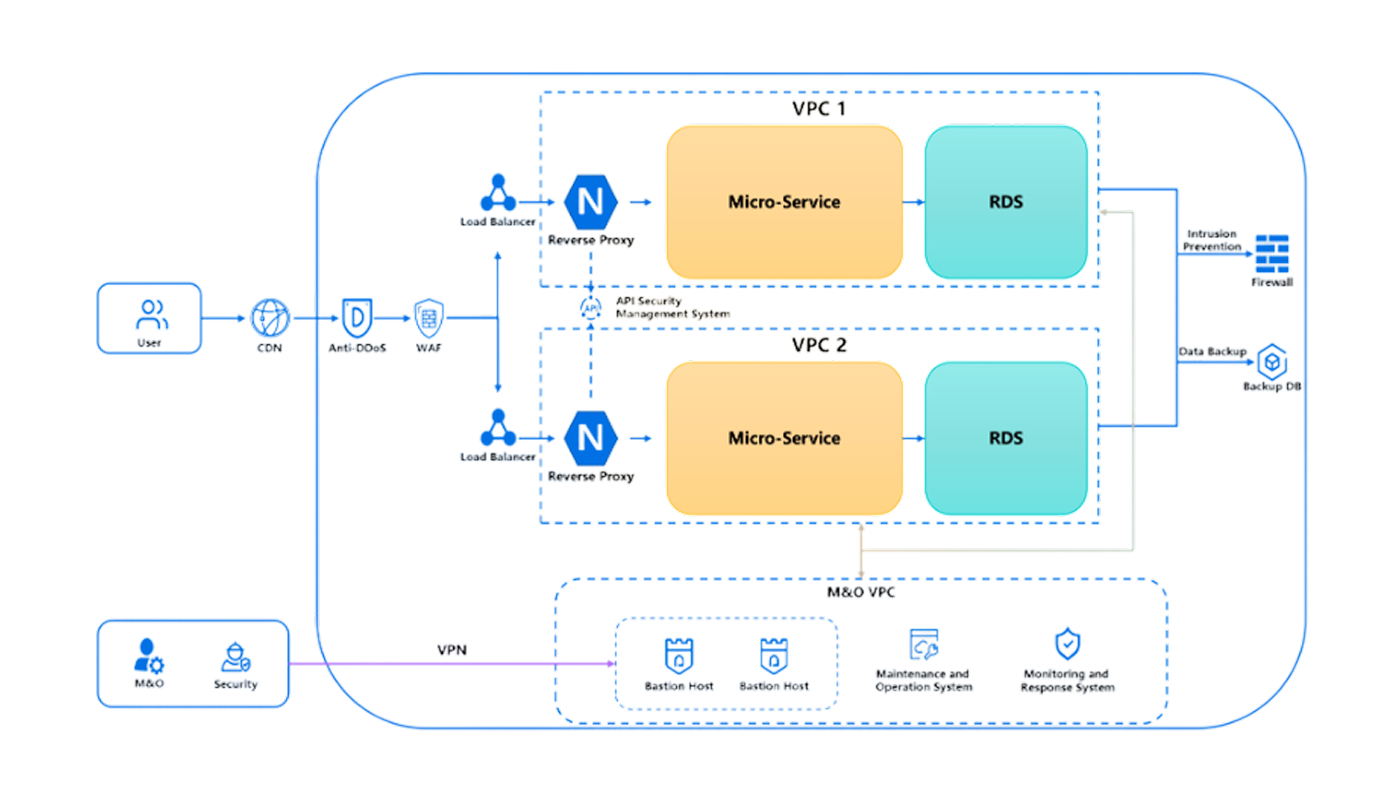
Threats from both external and internal sources could cause severe impacts on your business running on Kingdee’s cloud services. We have implemented comprehensive measures to safeguard it.
how we protect the system?
How we protect your data?
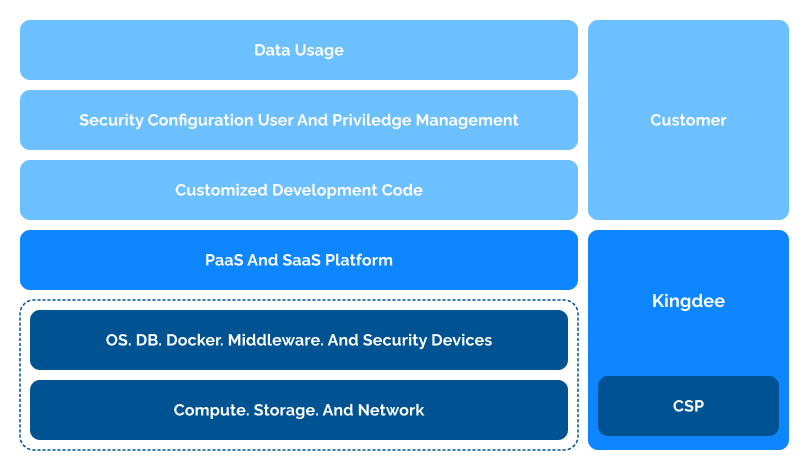
What we have done to protect your Assets?
How to report a security issue?
If you find or encounter any possible security vulnerability in Kingdee’s products or services, please notify Kingdee product security team.
Email:
Information that could help us locate, identify or mitigate vulnerability, such as requests with injection, screenshots of pop-out, prove-of-concept code, etc.
Your email will be confirmed as received within 24 hours and it may take a few days to verify the reported vulnerability. We will contact you through the sender’s email address if further communication or inform action is required.
Frequently asked questions
Kingdee uses an access control model based on RBAC (Role-Based Access Control), which defines different user permissions through roles. The model supports data access permission control at different granularities, such as the functional, field, and data levels.
Kingdee supports the access management strategy of separating the system administrator, security administrator, and audit administrator roles.
Kingdee’s public cloud utilizes renowned CSPs, which offer a complete security and privacy protection system, have obtained recognized security certifications (such as ISO27001, ISO27701, and CSA-STAR), and regularly receive SOC 2 attestation reports from third-party external audits.
Kingdee attaches great importance to your data assets and takes data protection as the core of its security strategy. Only authorized users can access the data, and data access permissions can be managed at different granularities, such as the functional, field, and data levels. For sensitive business data, Kingdee supports encryption using different encryption algorithms, such as common security encryption algorithms like Advanced Encryption Standard (AES)
Do note that Kingdee is only the custodian for the content data generated when you use cloud services; you have ownership and control over it. You are responsible for specific data security configurations and must therefore effectively ensure its confidentiality, integrity, and availability, as well as the authentication and authorization of data access.
Kingdee’s public cloud is currently deployed on servers in Singapore. Without your consent, Kingdee will not transfer your data to other regions. If you are located in countries other than Singapore or need to transfer data to other countries and require Kingdee’s assistance, you can contact Kingdee and sign Standard Contractual Clauses (SCC )or Model Contractual Clauses (MCC). Kingdee will deploy services overseas or transfer the data according to your authorization.
When using Kingdee cloud services, you should request Kingdee to configure cross-border security settings, which include encrypted data storage, data masking for display, encrypted transmission, etc. Your domestic branches and the foreign headquarters should sign EU-recognized SCCs. To mitigate risks, establish a security and privacy management system in accordance with the local regulation’s requirements, deploy cloud services locally, and de-identify personal information before transferring it to the foreign headquarters.

 EN
EN